OpenID Federation Final Release: Standarized and Scalable Trust Metadata
OpenID Federation 1.0 reaching Final status turns its trust chain, entity statements, and trust marks into a standardized way to express and automate trust metadata across ecosystems, beyond what classic PKI or emerging DID stacks can comfortably deliver at scale. This creates a common language to describe who can trust whom, for what, and under which policies for wallets, Agentic AI, open data infrastructures, and other digital ecosystems.
What OpenID Federation Final standardizes
At the heart of OpenID Federation are a handful of core components: Entity Statements, Trust Chains, Trust Anchors, and optional Trust Marks, all defined in terms of JWT-based metadata rather than certificates alone. Each Entity Statement bundles keys, endpoints, capabilities, and policy-relevant attributes into a signed JSON structure, which can be discovered and composed into a verifiable chain from a leaf entity up to one or more trust anchors.
Federation 1.0 also standardizes how metadata policy is applied along that chain, allowing higher-level operators and anchors to constrain subordinate metadata (for example enforcing FAPI profiles, algorithm requirements, or sector-specific claims) before the resolved metadata is used by relying parties or OpenID Providers. This turns “who is this?” and “under what rules?” into first-class, machine-readable concepts rather than static configuration scattered across systems.
OpenID Federation Final vs. other trust models
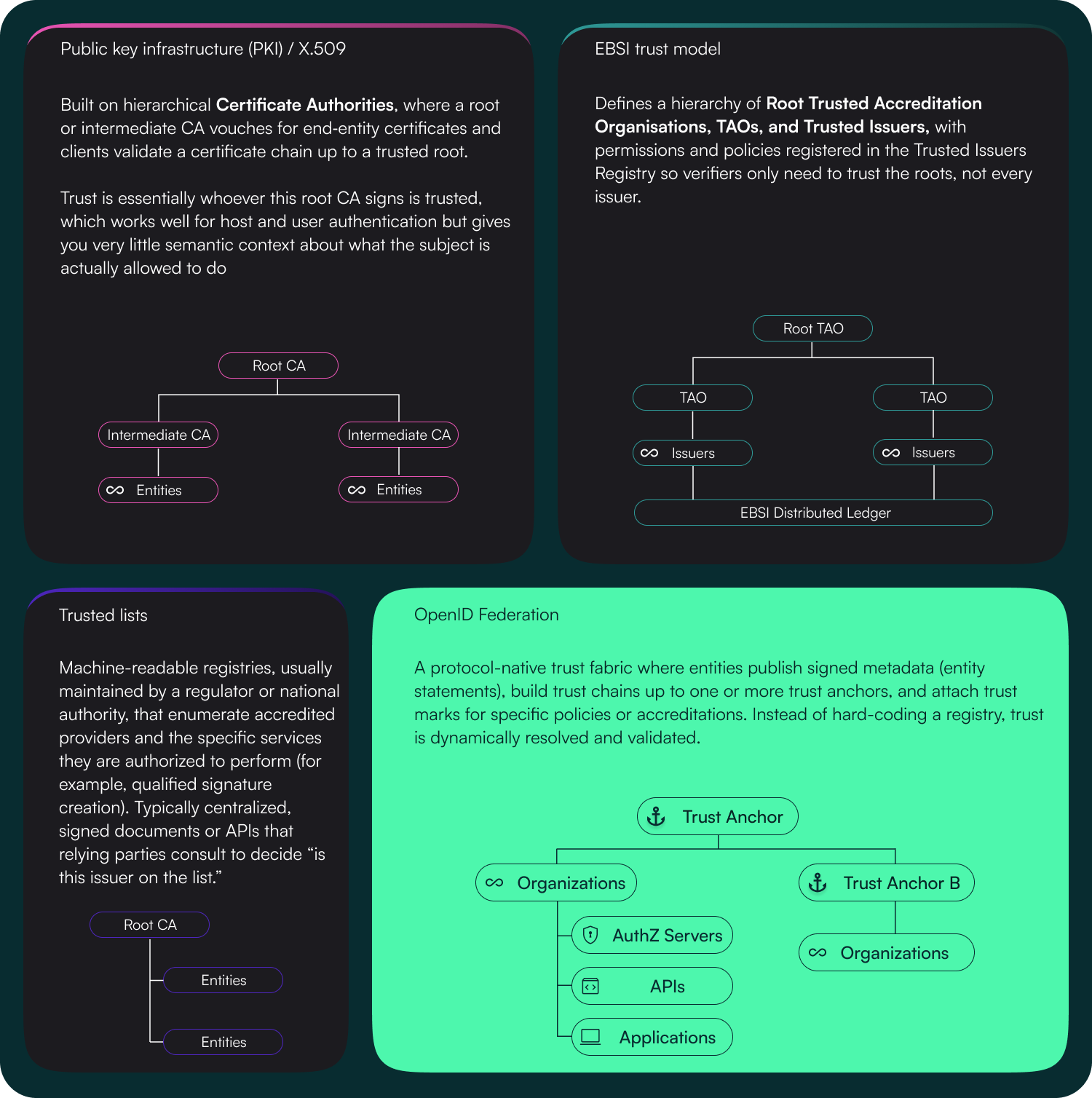
Today’s trust models are split between traditional PKI/X.509 hierarchies, SAML-style federations, and a fast-growing set of decentralized identity and wallet initiatives built on verifiable credentials and DIDs. Each stack carries its own way of describing who an entity is, what it can do, and which policies apply, which makes it hard to grow ecosystems without ever more bespoke onboarding and one-off integrations.
Trusted lists and the EBSI trust model prove that you can run serious ecosystems using curated registries of accredited issuers, but they stop at “who is allowed to issue what,” exposed via a domain‑specific API or smart‑contract registry like the Trusted Issuers Registry. EBSI’s Root TAO/TAO/TI hierarchy already looks like a trust chain, yet verifiers still need to hard‑code the EBSI registries and policy model into their stack, and the trust metadata they expose is tightly coupled to VC issuance rather than general protocol metadata.
OpenID Federation 1.0 Final steps in at precisely this point as a common trust metadata layer, standardizing how entities describe themselves, how that description is signed and delegated, and how policy is pushed and enforced across trust chains. With the Final Specification entering its review window, the technical contents are effectively locked, giving implementers confidence to treat Federation 1.0 as a stable base for long-term infrastructure.
Trust models at a glance
| Aspect | PKI / X.509 | EBSI trust model | Trusted lists | OpenID Federation 1.0 |
|---|---|---|---|---|
| Primary artifact | Certificates and certificate chains binding keys to identifiers. | Hierarchical registries (Root TAO, TAO, Trusted Issuers) and VC-focused trust data. | Curated registries of accredited entities exposed via domain‑specific APIs or registries. | Signed JWT Entity Statements, Trust Chains, and optional Trust Marks. |
| Focus of trust | Key ↔ identity binding (e.g. DNS, org identifiers). | Which issuers may issue which verifiable credentials in EBSI. | Which entities are allowed to participate or issue specific artifacts in a given scheme. | Endpoints, roles, capabilities, and policies for federation entities. |
| Policy expression | Limited to CA practice, OIDs, and external governance documents. | EBSI‑specific governance and policies hard‑coded into verifier stacks. | Scheme‑specific business rules tied to the list’s API or contract model. | Explicit metadata_policy applied and enforced along the trust chain. |
| Topology | Mostly hierarchical CA trees. | Root TAO → TAO → Trusted Issuers, effectively a fixed hierarchy. | Central or sectoral list operators, often one per scheme or jurisdiction. | Multiple trust anchors with overlapping, delegable hierarchies. |
| Update model | CRLs/OCSP, certificate renewal, and manual configuration updates. | Registry updates and VC governance changes deployed via EBSI components. | Periodic list updates, API polling, or contract events per registry. | Dynamic discovery and resolution of trust metadata at request time. |
| Fit for wallets & Agentic AI | Indirect; requires extra layers to express issuer, wallet, or agent capabilities. | Strong for EBSI VCs, but tightly coupled to that stack and policy model. | Works for specific schemes but does not generalize across protocols or ecosystems. | Direct, protocol‑native trust metadata for wallets, agents, and APIs across ecosystems. |
OpenID Federation Final and PKI/X.509
Traditional PKI/X.509 remains extremely good at binding keys to identifiers (like DNS names or organizational identities) through certificate chains, but it says almost nothing about higher-level protocol metadata or dynamic policy. If you want to know whether a given certificate-holder is allowed to act as an OIDC Provider in a FAPI profile, or which token algorithms they support, you are back to out-of-band agreements and static configurations.
OpenID Federation keeps PKI for cryptographic underpinnings but moves rich trust metadata into signed entity statements and policies, enabling use cases like automatic RP registration, ACME-driven certificate issuance limited to federation members, and multilateral, overlapping trust hierarchies without fragile CA cross-signing. Compared to SAML-based federations where operators periodically scrape and merge flat XML metadata aggregates, Federation replaces batch files with on-demand resolution of trust chains and derived metadata, which scales better as entities appear, rotate keys, or change roles.
Federation, DIDs, and verifiable credentials
Decentralized Identifiers (DIDs) and Verifiable Credentials focus on subject-centric identity, expressing claims about individuals, organizations, or devices in a way that can be verified across different ledgers and technologies. They are powerful for portability and user-controlled wallets, but they still leave open the question of who is permitted to issue which credentials, under which governance, and how verifiers discover trustworthy issuers at scale.
In addition to traditional federated trust, OpenID Federation 1.0 can coexist with decentralized identifiers (DIDs) and verifiable credential formats such as SD‑JWT‑VC and W3C VCDM. A hybrid model lets ecosystems keep governed onboarding and accreditation in a federation, while anchoring keys, status lists, and no‑call‑home verification on a decentralized verifiable data registry.
In this model, federation entities and DIDs reference each other
bi‑directionally, for example by using an alternativeEntityId in federation
metadata and DID documents that point back to federation identifiers or
endpoints. This creates cryptographic continuity across layers, so that the
same keys can underpin federation metadata, DID documents, issued credentials,
and even X.509 certificates.
For a deeper, implementation‑oriented look at how to build such hybrid ecosystems in practice—including issuer onboarding, credential issuance, and privacy‑preserving verification flows—see the dedicated blog post Hybrid Ecosystems: Combining OpenID Federation with Decentralized Identifiers (DIDs).
OpenID Federation 1.0 Final matters because it turns trust metadata into a standard, composable layer that wallets, Agentic AI, and open data infrastructures can all rely on without bespoke onboarding each time.
Why OpenID Federation final release matters
The OpenID Federation Final Release matters because it turns years of experimental, ecosystem-specific work into a stable, global standard for automating trust between identity, wallet, AI, and open data participants at internet scale.
Wallet ecosystems
For wallet ecosystems, Federation 1.0 Final provides a reusable backbone for trust registries so wallets can discover authorized issuers and verifiers via signed, machine-readable metadata instead of static whitelists. Trust anchors can enforce national or sectoral policy in one place, making it realistic to roll out cross-border or multi-scheme credential programs as VC standards mature.
Learn more about OpenID Federation for wallet ecosystems by reading the OpenID Federation: the Missing Link for Scalable Trust in Data, AI, and Wallet Ecosystems blog post.
Agentic AI and API access
For Agentic AI, treating agents as first-class federation entities—complete with signed metadata, allowed scopes, and trust marks—enables regulated marketplaces where API access and behavior are governed transparently. This replaces opaque, one-off integrations with verifiable declarations of what an agent is allowed to do, which APIs it can reach, and under which governance rules.
Learn more about OpenID Federation for Agentic AI by reading the Building Access Control for Agentic AI with OpenID Federation blog post.
Open data and regulated ecosystems
In open data ecosystems such as open finance, insurance, or energy, Federation 1.0 allows operators and regulators to replace ad hoc onboarding and manual due diligence with automated verification of accredited participants. Consistent policy distribution along trust chains means compliance requirements and technical profiles are enforced cryptographically across sectors and borders, rather than scattered across spreadsheets and configuration files.
Summary
OpenID Federation 1.0 Final standardizes a trust metadata layer that complements PKI, DIDs, and verifiable credentials instead of competing with them. By making “who is this entity, what can it do, and under which policies?” a signed, discoverable artifact, it gives wallets, agents, and open data platforms a common foundation to grow safely at internet scale.
Ready to put standardized trust metadata to work in your own ecosystem?
Request Sandbox Access →